
 |
|
|||||||
| OpenBSD General Other questions regarding OpenBSD which do not fit in any of the categories below. |
 |
|
|
Thread Tools | Display Modes |
|
|||
|
hi,
I'm wondering about how to manage something a bit difficult on openbsd. mainly we have several laptops running obsd (not only) ; but we have sometimes few things, manipulations to do, and while we're almost never connected from an individual connection, we were wondering about how to find a tool (without darknet/tor) whom permits this one, means NAT/PAT translation. in an idea, it would be for getting a teamviewer/anydesk like compatible tool : being able to see/control the remote desktop of opened session remotely, via a middle-man tool, to avoid changing settings of a public (or cell shared) internet connection ; unfortunately, I didnt found any (free) tool until there.. that's why Im asking for help there, with thice nicely drawn svg : 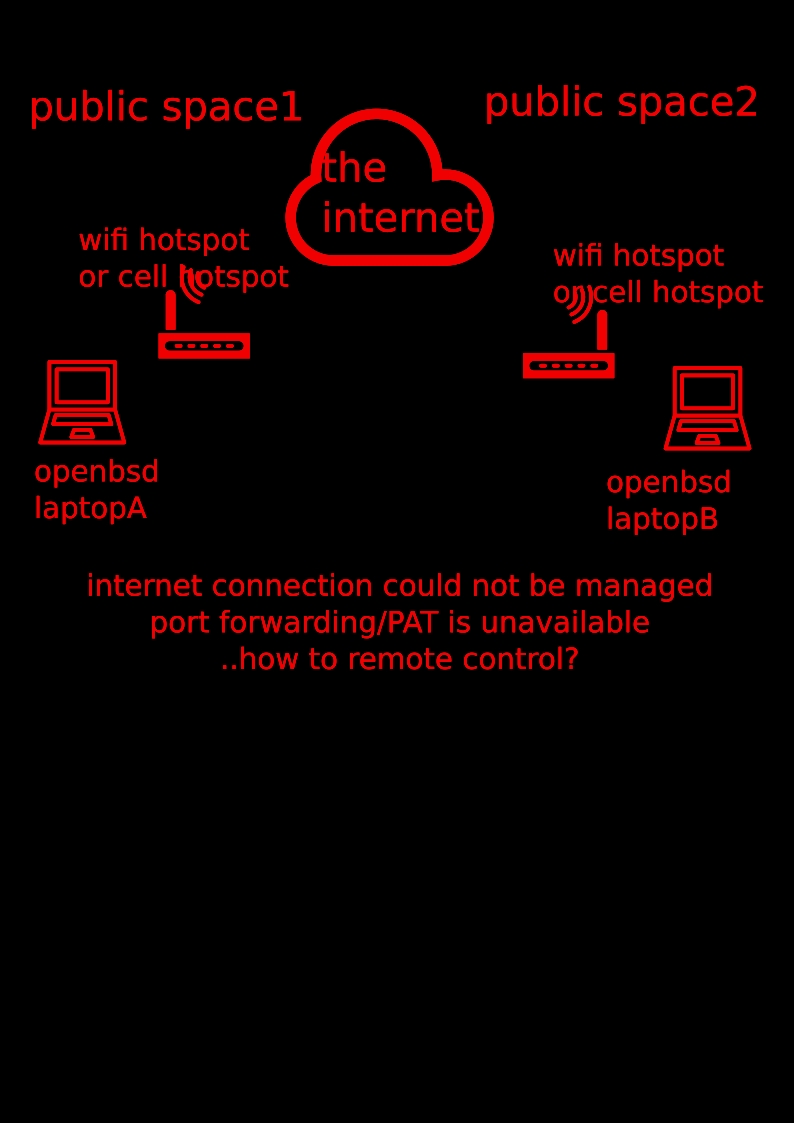 thank you! Last edited by hd77; 24th October 2022 at 12:55 PM. |
|
|||
|
thanks for your reply
in fact it's generally standard ipv4 with not port address translation. eg if Im connected to a coffee free wifi or hostel etc. the idea was, what tool to connect to another desktop by remote control, such as tamviewer or anydesk, but under openbsd, without port forwarding? thank you! |
|
||||
|
Here is an example where you have two cafes, in two locations, each with public Internet access. Both of these locations use RFC 1918 subnets for their patrons.
RFC 1918 addresses are defined within 3 address groups: 10/8, 172.16/12, and 192.168/16. These addresses are used for private networks, and are never routed over the Internet.Cafe A uses 192.168.100/24 for their guests, and connects to the Internet via an ISP that provides them with a single Internet-facing IP address: 198.51.100.17. Cave B uses 10.100.100/24 for their guests, and connects to the Internet via an ISP that provides them with two Internet-facing IP addresses: 203.0.113.5 and 203.0.113.6. They use one of these addresses for their business operation, and the other for sharing by their patrons.
----- The easiest way for these two devices to communicate privately over two public networks is with what is called a Virtual Private Network (VPN), which I mentioned in my first reply above. In the case of public networks such as found in these cafes, outbound traffic is used to establish NAT connection states. A third computer, already Internet connected and listening for incoming VPN traffic, would operate as the VPN's gateway router. OpenBSD comes with multiple VPN-capable services built in. IPSec, SSH, and WireGuard. Of these, in my opinon WireGuard is the simplest to provision and use. There are also third party VPN services and VPN clients available as packages, such as openvpn or vpnc. |
|
|||
|
Quote:
thank yu for replying well, isnt there any sort of "common" software for easy remote control then? or in a way to stand on IP networks : -it would ask for the service to let the subscibers communicate between them I guess -if there is one (maybe free?), how would it be possible to ensure the "remote control" of the desktop? I heard vnc was not secure nor reliable and slow.. could you tell a bit more about it? thanks! |
|
||||
|
OpenSSH is the common "remote control" tool used with OpenBSD. OpenSSH is available with many different OSes, widely used. It's a famous software project, which happens to be managed by OpenBSD developers.
But your initial question is about communication between two computers connected to private networks that you do not control, connected to the Internet via NAT routers. And you cannot have a computer at one of those locations "listen" for incoming packets to operate a service on that computer without having an administrator of the router provision that service in advance. Let's look at my example once more:
The router at Cafe B would drop any incoming traffic it did not expect. Only traffic initiated by devices on the local network would have state tracked by the router. If you want a device at Cafe B to "listen" for traffic and respond to packets, without initiating any outgoing traffic -- the router would need to know about the service and be provisioned to route the incoming traffic to the proper device in advance. This is often done by TCP or UDP port number, and is therefore called port forwarding. So, to "reach out" to a remote computer to control it, OpenBSD users will typically use OpenSSH, as it's built right in, is very secure, and very flexible in its capabilities. It can remotely provide shells and can forward SOCKS proxies and even forward graphics. But an SSH client cannot reach out to a listening SSH daemon sitting on a remote laptop at Cafe A or Cafe B, because those laptops only have private IP addresses that are not on the Internet, and the routers in those cafes have not been provisioned to forward traffic to the laptops. The "fix" is to add an Internet-facing service that each of these laptops can communicate with. Lets call it Service C: Both laptops can initiate communication from their respective cafes to Service C. NAT is involved with every packet, but no port-forwarding is required because the laptops initiate the communication, and the NAT routers just keep track of state. If Service C is a VPN, the two laptops can communicate with each other as if they were on their very own private network. One laptop could provide a listening service to the other. OpenSSH could certainly be used for "remote control" of one laptop from the other. |
 |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| openbsd, best remote control tool? | hd77 | OpenBSD General | 3 | 11th May 2022 10:28 AM |
| cannot use remote desktop | sw2wolf | OpenBSD General | 8 | 9th November 2017 10:46 PM |
| pf & remote desktop protocol | cerulean | FreeBSD General | 7 | 4th August 2011 10:14 PM |
| Remote desktop & terminal independence | Greg_Morgan | OpenBSD General | 10 | 22nd December 2009 11:07 PM |
| Revision Control Software | JMJ_coder | General software and network | 3 | 10th February 2009 04:19 PM |